Written by: Igor
Published: December 2025
Internet of things (IoT) application development is the process of building the software that powers connected devices. It’s a complex discipline that covers everything from the firmware on the hardware to the cloud backend and the user-facing application. Getting it right is challenging because it demands a rare mix of hardware, cloud, and software engineering skills.
The market is growing rapidly, with one Statista forecast predicting over 29 billion connected devices by 2030. This growth presents a massive opportunity for founders, but the path from idea to a scalable, secure product is filled with technical hurdles. This guide provides a practical framework for navigating the key decisions in IoT development.
You will learn:
- The core architectural layers and how to choose the right tech stack.
- A practical framework for managing the entire IoT data lifecycle.
- A multi-layered security strategy to protect devices, networks, and data.
- A phased roadmap for moving from proof of concept to full-scale production.
Choosing your IoT architecture and tech stack
Your IoT architecture is the blueprint for your entire product. The choices you make here will dictate scalability, running costs, and ultimately, what your users experience. Nail this foundation, and you're set up for the long haul in internet of things application development.
Think of the architecture in four basic layers: the devices themselves, the network connecting them, the data processing layer, and the application your users see. Each one builds on the last, so every decision matters.
This workflow gives you a good visual of how data travels from a physical sensor, gets processed along the way, and finally turns into something valuable for the end-user.
The great debate: edge vs. cloud
One of the first big forks in the road is deciding where to process your data. You can either handle it locally on the device (edge computing) or ship it all off to a central server (cloud computing). This isn't just a technical debate- it has huge business implications.
For example, an industrial monitoring system that needs to shut down a machine in milliseconds can't wait for a round trip to the cloud. It needs edge computing to analyze sensor data in real-time, right there on the factory floor. This slashes latency and can save a fortune in data transmission costs by only sending summaries or critical alerts upstream.
On the other hand, a smart home thermostat can happily send temperature data to the cloud. The cloud can then chew on historical patterns, pull in weather forecasts, and optimize heating schedules over time. A slight delay is no big deal. The right choice comes down to your product's specific needs for speed, cost, and connectivity. You can explore various application development models to see how this decision fits into your wider strategy.
Selecting the right hardware and connectivity
It all starts with the physical hardware- your sensors and devices. Your choice of microcontroller, sensor type, and power source directly hits your unit cost, battery life, and overall capabilities. A cheap temperature sensor for a smart farm has completely different needs than a high-fidelity camera for a home security system.
Once a device gathers data, it has to phone home. This is where communication protocols come in, and each one is a bundle of trade-offs between range, power draw, and how much data it can handle.
Choosing the right wireless protocol is all about balancing these trade-offs against your specific use case. A device plugged into a wall has very different constraints than one that needs to survive for five years on a single battery in the middle of a field.
Comparing common IoT connectivity protocols
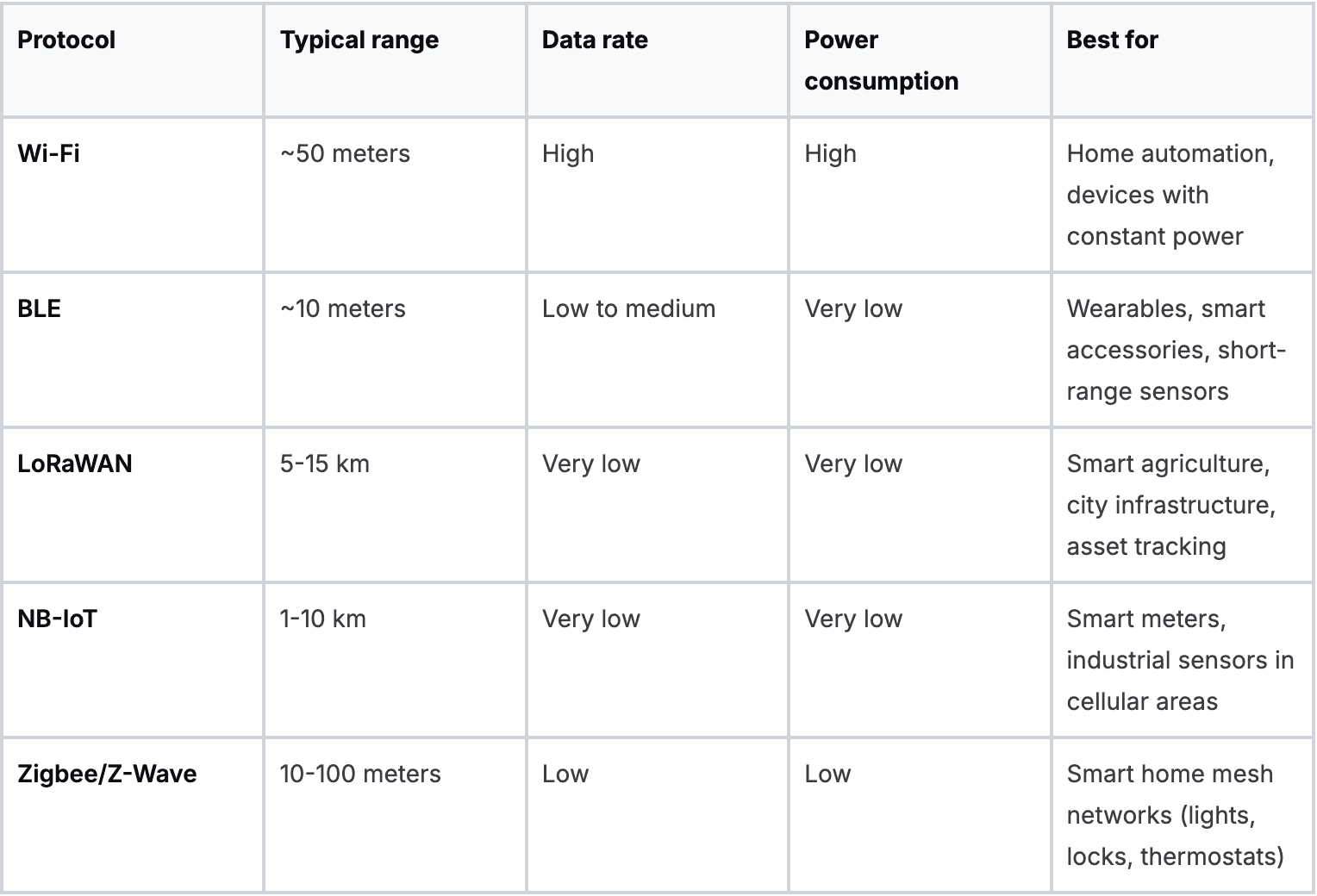
There's no single "best" protocol. The right answer depends entirely on whether you need to send a little bit of data a long way or a lot of data a short way, all while keeping your power budget in check.
Choosing your software and platforms
The software stack is what brings your hardware to life. For communication, MQTT (Message Queuing Telemetry Transport) has become the de facto standard for IoT. It’s incredibly lightweight and built to handle spotty networks, using a publish-subscribe model that's perfect for routing data from thousands of devices to a central point.
The final piece of the puzzle is your cloud platform- the command center for your entire operation. These platforms give you the tools to manage your fleet of devices, process incoming data, and build your actual application. According to a report from McKinsey, companies that adopt these platforms can cut deployment times significantly.
Big players like AWS IoT, Microsoft Azure IoT, and Google Cloud IoT offer soup-to-nuts toolkits for device management, data storage, analytics, and security. Picking one often comes down to your team's existing skill set, your specific needs, and the pricing structure. A solid platform doesn't just help you build; it gives you a scalable foundation to grow on.
Managing the flow of IoT data
In any IoT project, the data is the real prize. But when your devices start talking, it’s not a trickle- it's a firehose. One of the biggest operational hurdles you'll face is simply handling the sheer volume of information. You need a solid plan for the entire data lifecycle, from the instant a sensor takes a reading to its final destination in storage.
A well-thought-out data pipeline is non-negotiable. It’s what lets you collect, process, and store all that information reliably without drowning in it. The number of connected devices is exploding, with some analysts predicting the IoT market could generate over $1 trillion in annual revenue by 2030. This growth is fueled entirely by data.
Edge vs. cloud processing in action
The "edge versus cloud" debate is central to managing this data tsunami. This isn't an either-or choice; it's a strategic decision about what gets processed where. Get this right, and you'll save a fortune on bandwidth and slash latency.
Let's take a smart security camera as an example. Streaming raw, high-definition video to the cloud 24/7 would be prohibitively expensive. The data transfer and storage costs alone would sink the project. A much smarter approach is to use edge processing.
- Edge processing: An AI model runs right on the camera itself. It analyzes the video feed in real-time, learning to tell the difference between a person, a passing car, or just a tree swaying in the wind.
- Data filtering: The camera is programmed to only send clips to the cloud when it actually detects a person. Everything else is ignored.
- Cloud processing: The cloud now only receives the important, pre-filtered clips. This can cut bandwidth and storage needs by 90% or more. The cloud can then focus on higher-level tasks like long-term archiving, sending user alerts, and running deeper analytics.
This hybrid model gives you the best of both worlds: the immediate responsiveness of the edge combined with the massive storage and analytical power of the cloud.
Choosing the right database for IoT data
Once your data makes its way to your central system, it needs a home. But not all databases are cut out for the unique demands of IoT. To manage the constant stream of information from your devices, you first need to understand what is streaming data and how does it work. This knowledge is key to picking the right storage solution.
Your choice of database really depends on the kind of data you're collecting and what you plan to do with it. In IoT, two patterns usually emerge:
- Time-series databases (TSDB): These are purpose-built for data points that have a timestamp. They're brilliant at ingesting huge volumes of sequential data, like temperature readings from a factory sensor every single second. If your main goal is monitoring trends over time on a dashboard, a TSDB like InfluxDB or TimescaleDB is a fantastic fit.
- Data lakes: On the other hand, if your aim is to train machine learning models or run complex, exploratory queries, a data lake makes more sense. Data lakes are designed to store enormous amounts of raw data in its original format. This gives data scientists the flexibility they need to pull together diverse datasets for training an AI model that could predict equipment failure or optimize a city's energy grid.
Picking a database isn't just a technical footnote- it's a core business decision. A good time-series database can make your dashboards up to 100x faster than a traditional relational database. Meanwhile, a data lake provides the raw material you need to build a long-term competitive advantage with AI.
Ultimately, the goal is to build a data architecture that is both cost-effective and ready to scale. By processing data intelligently at the edge and choosing the right storage tools in the cloud, you lay a resilient foundation for your application. Working with expert data engineering services can be invaluable here, helping you design a pipeline that supports your business goals from day one.
Building a bulletproof IoT security strategy
In IoT, security isn't a feature you can bolt on at the end. It has to be baked into your product from the very first line of code. A single weak link- a vulnerable device in the field or an unencrypted data stream- can put your entire system and your customers' trust on the line.
Building a multi-layered defense is the only way to go. You have to think about security at every single level of the stack. The physical device needs protection, the network communication has to be locked down, and your cloud backend must be hardened against attack.
Securing the chain from device to cloud
True IoT security is an end-to-end discipline. You can't just secure your cloud and hope for the best with thousands of devices out in the wild. Each layer has its own unique threats and needs its own protections.
A rock-solid security model for internet of things application development covers these core areas:
- Device security: This is your frontline defense. It all starts with a secure boot process, which guarantees that only trusted, signed firmware can run on the device. This stops attackers from loading malicious code onto your hardware. Don't forget physical security, either- protections against tampering are vital for any device that's publicly accessible.
- Network security: The moment data leaves the device, it's vulnerable. Any and all data in transit must be encrypted using proven protocols like transport layer security (TLS). Think of it as creating a secure, private tunnel between the device and your cloud, making the data completely unreadable to anyone trying to eavesdrop.
- Cloud security: Your cloud infrastructure is the brain of the operation, making it a prime target. Here, security means locking down your APIs, using strict identity and access management (IAM) policies to control who can do what, and constantly auditing your systems for vulnerabilities.
Imagine a connected insulin pump. A security breach isn't just a data leak; it could be life-threatening. The device must use secure boot to ensure its core software is legit. All communications, like dosage instructions from a doctor's portal, have to be encrypted with TLS. And the cloud platform managing patient data needs to be locked down. There's zero room for error.
Navigating the maze of compliance
Beyond the technical side, you have to deal with a growing web of regulations. Depending on your industry and where your customers are, you could be on the hook for some seriously strict data privacy and security laws.
Two of the big ones you'll run into are:
- GDPR (general data protection regulation): If you have any users in the European Union, GDPR is non-negotiable. It dictates exactly how you collect, process, and store personal data. Get it wrong, and you're looking at massive fines.
- HIPAA (health insurance portability and accountability act): For any application handling protected health information (PHI) in the United States, HIPAA compliance is mandatory. This requires stringent security controls designed to protect patient privacy above all else.
To build a truly tough security framework, you have to get familiar with the common IoT security challenges that specifically target smart devices. The enterprise IoT market is exploding, projected to hit USD 1,819.2 billion by 2032 (source: Precedence Research), with device connections reaching billions. This growth makes security and compliance more critical than ever.
Your IoT security audit checklist
This isn't an exhaustive list, but it's a solid starting point that covers the foundational checks you need to run to catch the most common- and dangerous- vulnerabilities.
- Nuke all default passwords. Are any devices or services still using factory-default credentials? This is the lowest-hanging fruit for attackers. Change them.
- Verify encryption everywhere. Is data encrypted both in transit (with TLS) and at rest (in your databases)? Assume nothing.
- Review physical device access. Are your devices physically secure? Could someone just walk up and plug into a port?
- Lock down your update process. Do you have a secure way to push firmware and software updates over-the-air (OTA)? This is essential for patching vulnerabilities after deployment.
- Scan your third-party libraries. Are you using any open-source libraries with known vulnerabilities? Use scanning tools to check your dependencies regularly.
- Enforce strong API authentication. How are you making sure only authorized apps and users can hit your APIs? Implement robust authentication and authorization.
Think of this checklist as a way to start building a culture of security. It forces you to move from abstract ideas to concrete actions that will genuinely harden your IoT application against real-world threats.
A phased roadmap from pilot to production
Getting your IoT idea from a whiteboard sketch into a user's hands is a journey. A classic mistake is trying to do it all in one giant leap, aiming for a single, massive launch. The smarter, more capital-efficient path is to move through distinct, iterative phases. This lets you test assumptions, get real feedback, and reduce risk at every step.
This roadmap breaks that journey down into manageable stages, each with its own clear goals.
Phase 1: Proof of concept (PoC)
The goal here is brutally simple: prove your core idea is technically possible. A PoC isn’t for customers; it's for you and your investors. It’s a scrappy, quick experiment to answer one question: "Can we even make this work?"
At this point, you're grabbing off-the-shelf hardware like Raspberry Pis or Arduinos and stitching together existing software libraries. The focus is 100% on function over form. For instance, if you're building a smart soil moisture sensor, your PoC might just be a sensor wired to a dev board that sends a single reading to a free cloud dashboard. You've proven the basic data link works.
The PoC should be fast- a few weeks at most- and cheap. Its only job is to give you the green light to move forward with confidence.
Phase 2: Custom prototype
You've proven it's not science fiction. Now, the focus shifts to real functionality and what the user actually experiences. The prototype is the first version that starts to look and feel like a real product. Here, you'll graduate from dev kits to custom-printed circuit boards (PCBs) and design a basic enclosure, probably 3D-printed.
The whole point is to create something a small group of friendly users can actually get their hands on. The software is still raw, but it should showcase the main features. Sticking with our smart sensor example, your prototype would now be a self-contained unit with a battery, sending regular moisture readings to a simple mobile app.
This is where you collect your first real user feedback. Does it solve their problem? Is it a pain to set up? What's missing? This feedback is pure gold and will directly shape the next version of your product.
Phase 3: Pilot program
A pilot is your dress rehearsal for the real world. You’ll manufacture a small batch of devices- typically 50 to 200 units- and get them into the hands of a select group of early-adopter customers in their actual environment. This isn't a lab test anymore; it's a live-fire exercise.
The goals for the pilot are clear:
- Validate the entire system at a small scale: Test everything from unboxing to connectivity, data accuracy, and battery life in the wild.
- Gather real-world performance data: How do your devices handle different environments? Is the battery life what you predicted?
- Refine your operations and support: How will you handle a customer call? What does your remote device update process actually look like?
Feedback from the pilot is critical for squashing bugs, fine-tuning the user experience, and truly understanding the value you're delivering. This phase gives you the final validation you need before hitting the big red button on mass production.
This whole process highlights just how important it is to build a layered security and operational model, covering the device, the network, and the cloud.
This flow drives home that security can't be an afterthought. It has to be baked in at every single stage.
Phase 4: Full production and scale
This is the final step. It's time to scale up. Moving to full production is a major undertaking that involves significant investment and meticulous planning. You’ll be finalizing deals with a contract manufacturer (CM), locking down your supply chain, and prepping for mass distribution.
Key activities at this stage include:
- Design for manufacturability (DFM): Work with your CM to tweak your hardware design so it can be built efficiently and cost-effectively at scale.
- Robust monitoring: Implement serious dashboards to track the health, uptime, and performance of your entire fleet of devices.
- Scalable infrastructure: Your cloud backend needs to be ready to handle the traffic from thousands, or even millions, of devices without breaking a sweat.
The leap to production is a huge milestone that demands tight management of logistics, quality control, and customer support. For a much deeper look into this final stage, our guide on the deployment of applications offers some great insights for making this transition as smooth as possible. Sticking to this phased approach ensures you're building a product that is not just technically solid but also validated by the market and ready to grow.
Defining success and preparing for scale
Getting your IoT application launched is a huge milestone, but it's the starting pistol, not the finish line. Now the real work begins: proving value, measuring what matters, and getting ready to grow.
Success in internet of things application development isn't just about a smooth deployment. It's about building a resilient system that delivers consistent value and scales without breaking the bank. To pull that off, you need to look past the vanity metrics and get brutally honest about what's working- and what isn't.
Technical KPIs vs. business metrics
It's tempting to get lost in a sea of technical data, but you need to separate the signal from the noise. The key is to draw a sharp line between the technical health of your system and the business value it creates. They're both critical, but they tell very different stories.
Think of technical key performance indicators (KPIs) as the vital signs of your IoT fleet. A few core technical KPIs you have to watch:
- Device uptime: What percentage of your devices are online and reporting? A sudden dip is a massive red flag.
- Battery life: Are your devices hitting their projected battery performance? If they're draining faster than expected, you have a serious user experience and maintenance cost problem.
- Data latency: How long does it take for a data point to travel from a sensor to your cloud application? High latency makes time-sensitive solutions useless.
But a technically flawless system that nobody uses is still a failure. This is where business metrics come in. These are the numbers that tell you if you’re actually solving a real problem. Your most critical business metrics should include:
- User engagement: Are people actually using your application? How often are they logging in? Are they using key features?
- Return on investment (ROI): Can you prove with hard numbers that your IoT solution is saving customers money or boosting their revenue?
- Churn rate: What percentage of customers are canceling their service? High churn is the clearest possible sign of a product-market fit problem.
Exposing the hidden costs of scale
As you gear up for growth, you need a crystal-clear picture of your total cost of ownership (TCO). The upfront hardware cost is just the tip of the iceberg. The real expenses in IoT are almost always recurring.
These hidden costs often hide in plain sight:
- Data transmission: Cellular and satellite data plans might seem cheap for a handful of devices, but they can become a massive operational expense at scale.
- Cloud services: Storing and processing petabytes of sensor data isn't cheap. Your cloud bill will grow in direct proportion to your device fleet.
- Device maintenance: What's your plan for when a device fails in the field? Rolling a truck to send a technician to replace a single sensor can instantly wipe out years of profit from that unit.
Getting a handle on these costs is non-negotiable. It’s the only way to build a pricing model that actually works and an infrastructure that won't crumble under its own weight.
Wrap-up
Successfully navigating internet of things application development requires a strategic, phased approach. By focusing on a solid architecture, secure-by-design principles, and a clear-eyed view of both technical and business metrics, you can avoid common pitfalls. The single most important thing to do next is to validate your core technical assumptions with a rapid proof of concept. Don't over-engineer; just prove it can work.
We at N² labs can help you build the right IoT architecture and navigate the complexities of hardware, software, and cloud infrastructure.
FAQ
The biggest hidden costs are almost always recurring operational expenses. The top three are data connectivity fees that balloon at scale, ever-growing cloud service bills for data storage and processing, and the high cost of physical device maintenance and support in the field. Founders often underestimate these long-term costs.
For most startups, an off-the-shelf platform like AWS IoT or Azure IoT is the smarter choice. They accelerate development by providing pre-built tools for device management, security, and data pipelines. A custom build offers more control but is far more complex and expensive. It only makes sense for companies with highly unique requirements or those operating at a massive scale where platform fees become prohibitive.
The best language depends on the part of the IoT stack. For firmware on resource-constrained devices, C and C++ are the standard due to their performance and low-level control. For edge gateways that perform local data processing, Python is very popular because of its strong data science libraries. For the cloud backend and application layer, languages like Java, Python, and Node.js are all common and effective choices.